SOLUTIONS
KEYPASCO ZTNA
Zero Trust(ZTA) Solution
The Keypasco Zero Trust Solution is a government-certified system for diverse devices and cloud environments, enabling continuous authentication to secure cross-system and remote access. Compliant with NIST, CISA, and ISO 27001, it enforces strict identity verification and access control in line with Zero Trust principles.

Leading Enterprises into the New Era of Zero Trust with Three Core Authentication Mechanisms
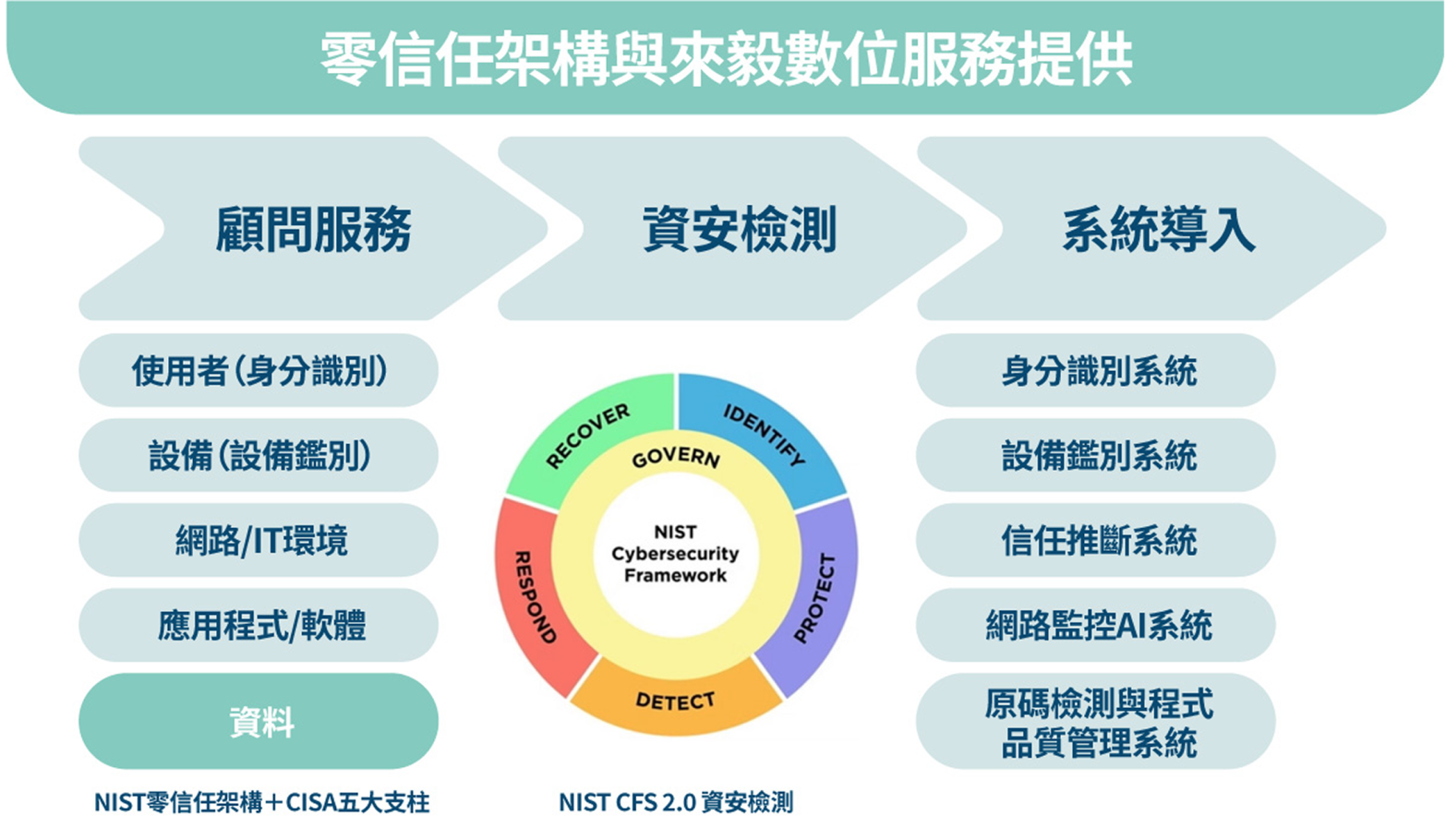
As Taiwan advances Zero Trust adoption for top-level public institutions, Keypasco supports this policy with NICS Phase 1 and 2–certified identity and device authentication solutions, compliant with government regulations.
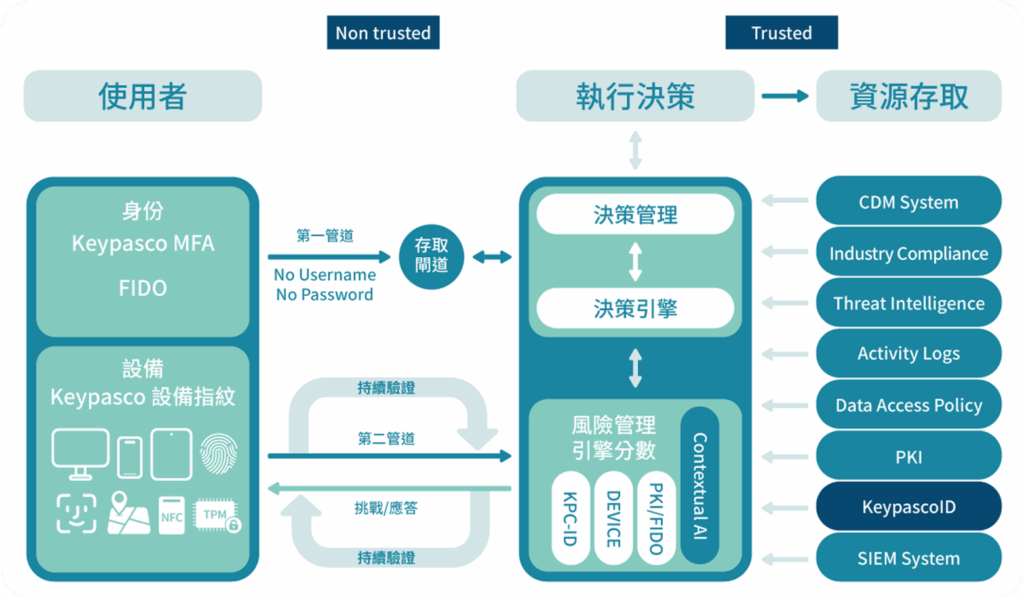
Following NICS and NIST SP 800-207 guidelines, our resource portal-based architecture integrates identity, device, and trust inference to secure cloud and remote access. With two-channel authentication, device fingerprints, and risk assessment, we enable “Never Trust, Always Verify” while seamlessly fitting into existing systems—strengthening defenses for governments and large organizations.

Identity Authentication

Device Authentication

Trust Inference
Three Core Mechanisms of Keypasco Zero Trust Architecture
The Keypasco Zero Trust architecture follows the principle of “Never Trust, Always Verify,” combining MFA/FIDO authentication, device fingerprints, and risk scoring for multi-layered, cross-channel security.
Users authenticate without usernames or passwords via two-channel verification and risk assessment. A policy engine with contextual AI scores risk in real time and integrates with CDM, SIEM, logs, and compliance tools, making it ideal for governments, critical infrastructure, and large organizations to secure every access request for both internal and remote environments.

Traditional Architecture vs. Zero Trust Architecture
| Phase | Traditional Approach | Zero Trust Approach |
|---|---|---|
| Identity Authentication | Login with username/password; access control often based on static role settings. |
|
| Device Authentication | No TPM or agent binding; device health not assessed; any device with credentials can log in. |
|
| Trust Decision – | Single-factor trust based on credentials; no additional verification even during suspicious activity. |
|
What Makes the Keypasco Zero Trust Solution Stand Out
Identity Authentication
Keypasco’s MFA follows NICS Zero Trust guidelines and ISO 29115 standards.
With device fingerprints, two-channel authentication, and extended factors (geolocation, time-based controls, risk scoring), it greatly reduces the risk of credential compromise, eavesdropping, or misuse.
Supports multiple MFA modes, FIDO UAF and FIDO2 certification, and passwordless authentication using personal devices—reducing token management complexity and increasing flexibility.
Also supports FIDO tokens and consistent security standards for internal staff, third-party vendors, and cross-institution collaborations.
Device Authentication
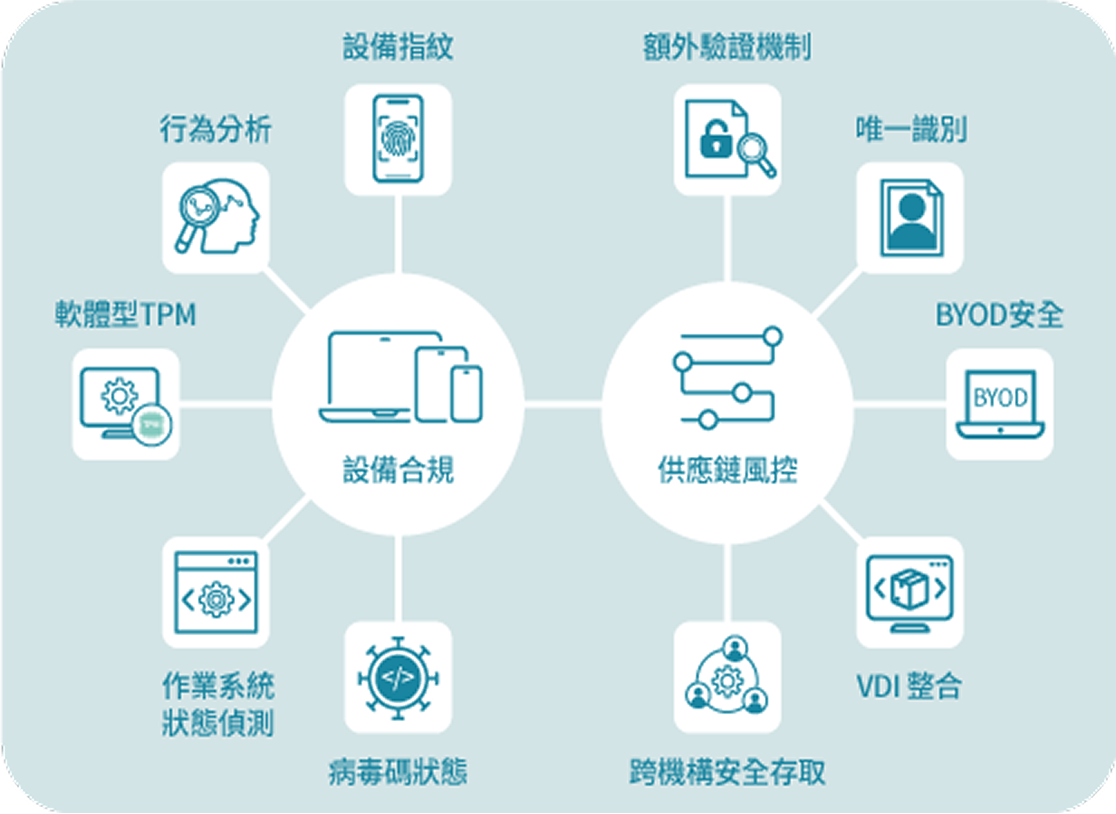
Device Compliance
Uses device fingerprints and behavioral analytics to perform hardware-free device inventory and identification, detect unmanaged devices, and enforce risk control. Integrates with EDR for device security evaluation and provides software TPM for desktops/laptops.
Supply Chain Risk Control
Evaluates BYOD and external partner devices to ensure security levels match internal devices. Dynamically adjusts access rights or requires extra authentication. Can integrate with VDI for enhanced cross-organization access security.
Trust Inference: Network Layer
Precision Control for Secure Network Access
Implements Zero Trust Network Access (ZTNA) to enforce least privilege and end-to-end encryption, restricting connections by identity, device risk, and context. All data is transmitted via HTTPS to ensure confidentiality and integrity.

Trust Inference: Application Layer
Real-Time Zero Trust Protection
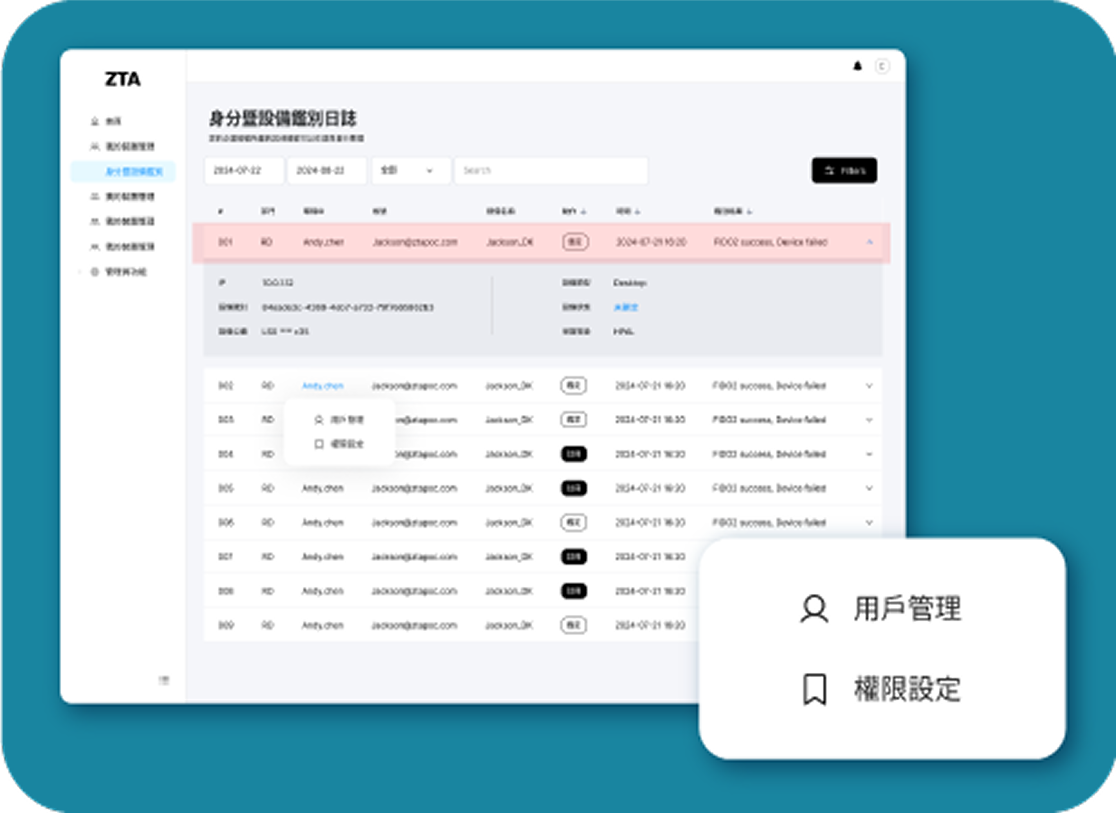
In Keypasco’s Zero Trust architecture, identity authentication, device recognition, and dynamic risk assessment strengthen application access control. The system adjusts permissions based on task attributes and role risk levels, automatically applying MFA or restricting operations to enforce least privilege.
For privileged accounts, dedicated authentication and risk controls prevent misuse, while behavior analytics and access logs enhance security without impacting usability.
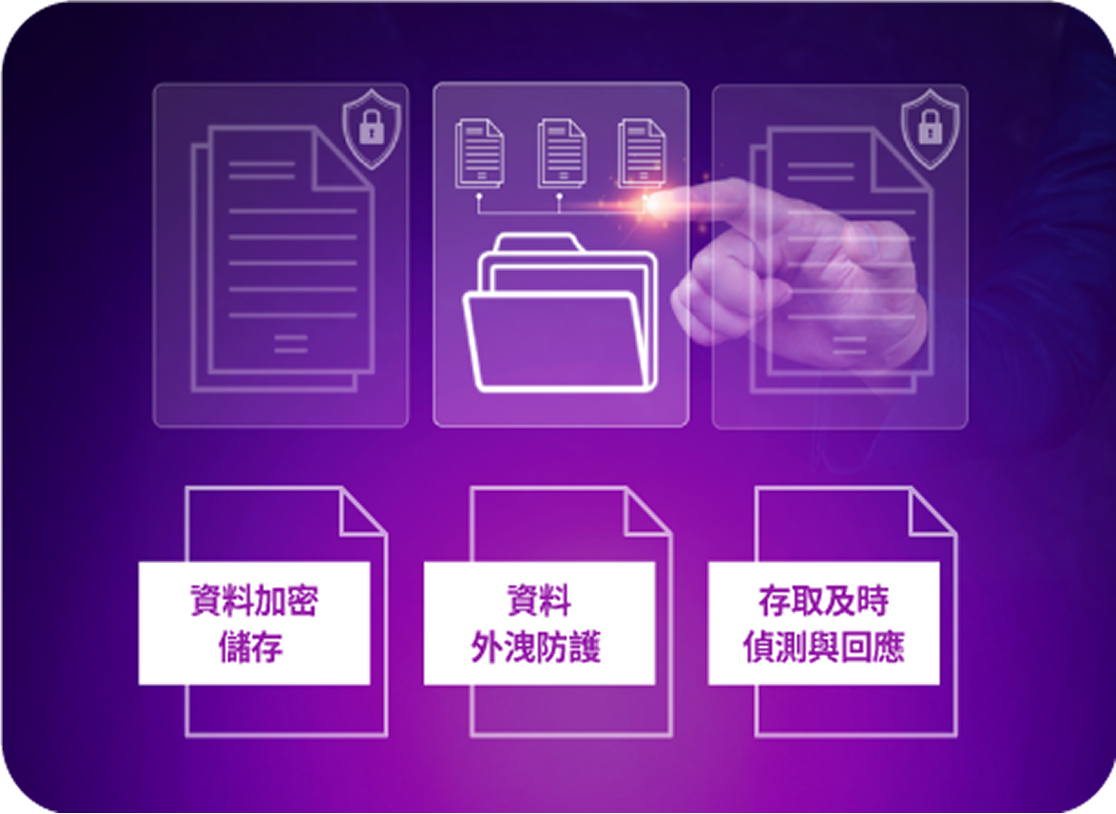
Trust Inference: Data Layer
Secure Data Access Strategies
While not a DLP tool, Keypasco mitigates sensitive data leakage at the source through risk assessment and identity verification. Dynamic risk scoring and adaptive policies adjust access conditions in real time, blocking unauthorized devices or accounts. This complements DLP solutions by adding a proactive layer of access control and prevention.
Keypasco ZTA Enterprise Deployment Overview
在未導入 Keypasco 之前,用戶登入企業網路服務時僅依賴帳號密碼,無法有效防範帳號盜用與釣魚攻擊。企業若有強化驗證流程的需求,便可透過 Keypasco Platform API 進行彈性整合。Keypasco 會依企業提出的身份驗證需求,導入客製化的 MFA(多因素驗證)機制,包含設備指紋、雙通道架構、地理與時間管理、近場認證與風險評估引擎等功能。導入後,使用者依然維持原有登入方式,但背後已無縫整合 Keypasco 的雙通道驗證與防釣魚技術,顯著提升整體服務安全性,同時不影響用戶體驗。

Recommended Server Specifications
Deployment Options
On-Premises
Supported Databases
Support Microsoft SQL Server, PostgreSQL, SQLlite
Supported Server Operating Systems
Supports Commercial RedHat 8 & 9, Ubuntu 18 – 24, Windows Server 2016 or later
Supported Mobile OS
Android 7 or later, iOS 12 or later
Supported Browsers
Firefox, Google Chrome, Microsoft Edge, Safari
LATEST NEWS
Master cybersecurity trends to build a foundation of competitiveness

Feature One

Feature Two

Feature Three
Strengthen Your Identity Authentication Now Elevate Enterprise Security Like Never Before
Keypasco is delighted to share more about our exclusive technologies and products with you! Tell us your needs and goals, and let Keypasco deliver the most suitable solution—becoming your dedicated identity authentication technology advisor.
如果您想問技術相關問題 請點我
