OUR AWARDS & PATENTS
With innovative multi-factor authentication (MFA) technologies and a Zero Trust framework, Keypasco has earned multiple international cybersecurity awards and holds patents in multiple countries, covering device fingerprinting, two-channel authentication, and risk assessment. Driven by R&D innovation, we deliver the most secure and forward-looking authentication solutions to customers worldwide.
Awards

2024 Cybersecurity Award

2022 SelectUSA Cybersecurity Winner

2018 Top 10 Managed Security Service Provider

2016 Red Herring Top 100 Europe Award

2016 CMA Contactless & Mobile Award

2014 APICTA Excellence Award in Finance

2024 資安精品獎

2022 SelectUSA 網路安全第一名

2018 年十大頂尖的資安託管服務商

2016 紅鯡魚全球科技創新大獎

2016 CMA 非接觸式與行動應用獎

2014 APICTA 金融類傑出表現獎
Our Patents
Keypasco holds 68 patents across 16 countries, including the U.S., Japan, Taiwan, South Korea, the EU, China, and Singapore. These patents cover core technologies such as device fingerprinting with two-channel authentication for stronger identity binding, proximity authentication for physical device security, central private key splitting to prevent misuse, and dynamic URL authentication paths for multi-tenant environments.
We also push forward passwordless adoption, enabling secure, trusted access without usernames or passwords.
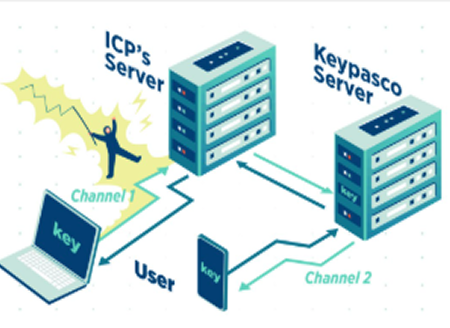
Device Fingerprints & Two-Channel Authentication
Patent: Method for Verifying Identity via User Location
Patent Publication No. I531202
When logging in or performing sensitive transactions, Keypasco’s patented device fingerprinting identifies unique hardware/software traits to bind devices securely. Combined with two-channel authentication—linking a user’s registered devices such as phone and computer—this mechanism blocks unauthorized devices, phishing, and credential theft, providing an invisible yet robust defense.
Two-channel Structure
Device Fingerprints

Proximity Authentication
Patent: Network Security Authentication Method and Portable Electronic Device Authentication Method
Proximity authentication uses physical distance as a security factor. The user’s registered device (e.g., phone, wearable) must be near the login device, verified via Bluetooth, NFC, or ultrasound. This ensures both devices belong to the same user, blocking remote hijacking attempts—ideal for high-security MFA scenarios.
Centralized PKI with Private Key Splitting
This approach splits a private key into two halves—one stored securely on a central server, the other encrypted and stored in the user’s device app. Both must match during authentication, reducing key theft risks even if the device is lost or compromised.
Dynamic URL Authentication
Dynamic URL is a flexible and highly scalable authentication architecture that allows the same client or application to automatically route multiple ICPs (service providers) to multiple IDPs (identity providers) based on different service requirements. This design enables enterprises to easily integrate various authentication sources without having to develop a separate login process for each service, thereby improving deployment efficiency and operational flexibility. At the same time, the dynamic URL mechanism also facilitates multi-tenant, multi-brand, or cross-regional authentication needs, delivering a consistent and scalable secure login experience for enterprises.
Key Management System
Encrypted private keys are bound to a device’s unique fingerprint, preventing decryption or use on unauthorized devices. This stops key duplication, tampering, or misuse, ensuring the key’s authenticity and exclusivity.
Passwordless Login Environment
Patent: Method and System for Logging into an Online System Without Account Name and Password
In application environments where no specific account or password is required for login, authentication evolves toward true passwordless access. Users no longer need to remember complex account-password combinations; instead, they are securely authenticated and logged in through trusted devices, biometric verification, or certificate-based authentication. This approach not only greatly simplifies the login process and enhances user experience but also reduces cybersecurity risks caused by password leaks, reuse, or phishing attacks—making it a critical step toward achieving both security and convenience.
LATEST NEWS
Master cybersecurity trends to build a foundation of competitiveness

Feature One
Lorem ipsum dolor sit amet, consec tetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis.

Feature Two
Lorem ipsum dolor sit amet, consec tetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis.

Feature Three
Lorem ipsum dolor sit amet, consec tetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis.
Strengthen Your Identity Authentication Now
Elevate Enterprise Security Like Never Before
Keypasco is delighted to share more about our exclusive technologies and products with you! Tell us your needs and goals, and let Keypasco deliver the most suitable solution—becoming your dedicated identity authentication technology advisor.
如果您想問技術相關問題 請點我





